Infiltrating an enemy base is a rather difficult task. Multiple security measures are implemented to prevent any form of intrusion, challenging even the most skilled of infiltrators.
The WEC training facilities however can provide any amateur operative with enough knowledge and gadgets to tackle even the most advanced security measures and overcome any and every obstacle in their way. What follows is a list of the security measures an infiltrator is most likely to encounter during their mission, as well as certain obstacles.
#1 - The Keypads: The most widely used form of preventing intrusions. A keypad is a locking mechanism that is attached to an electrical door. The door will only be opened only if the correct code is entered on the keypad and if the fingerprints of the user match someone with a high enough clearance level.

After months of research, WEC has developed a device that scans the keypad for security weaknesses and pinpoints them. The device however is still a non-user friendly prototype and additional instructions are required to operate it.

Each keypad assigns different ID numbers to different parts of it's circuitry, the device then detects each ID and the ID of the security sectors. The user must then click on the required security IDs to cause the sectors to be re-initialised and acquire a random new ID. Once all traces of security are gone, the device forces the keypad to open the door, disabling further functionality while doing so.
Re-initialising a sector that is not part of the security will send a signal to the main server, informing it of the intrusion. That will cause it to issue an area lockdown warning. After three warnings, the area is locked down and the mission is considered a failure.
#2 - : Laser Turrets: A classic and an old favourite to any powerful and paranoid fellow, the lasers are an efficient way of detecting movement. Attached to a turret spells trouble for any infiltrator; one wrong step could trigger it's powerful machinegun and terminate a mission in the most unfortunate of manners. Turrets are usually placed in maze-like formations in order to both further confuse enemy agents and provide a valid route to whatever is being guarded. After all, the owner of the turrets should not be locked out of their own property.
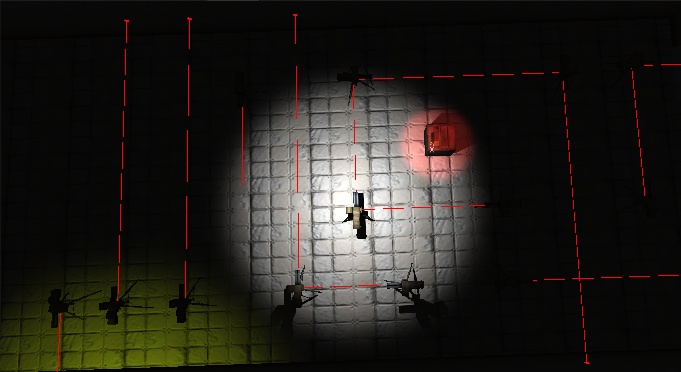
The WEC research facilities have once again developed two extraordinary pieces of technology that allow the infiltrator to avoid any danger of death.
The first one comes in a package with the Black outfit, it is a cutting-edge cloaking device. Using the basic principles of light refraction, the cloaking device virtually allows light to pass through you, making you impossible to detect by visual means. However, due to the large power consumption, it can only remain active for three seconds before it enters a cooldown period of 37 seconds in which it cannot be used. Furthermore, fast movement seems to disrupt it's effects, rendering the agent visible again.
The second piece of technology is a lense that allows it's wearer to view the routes of a laser's light.
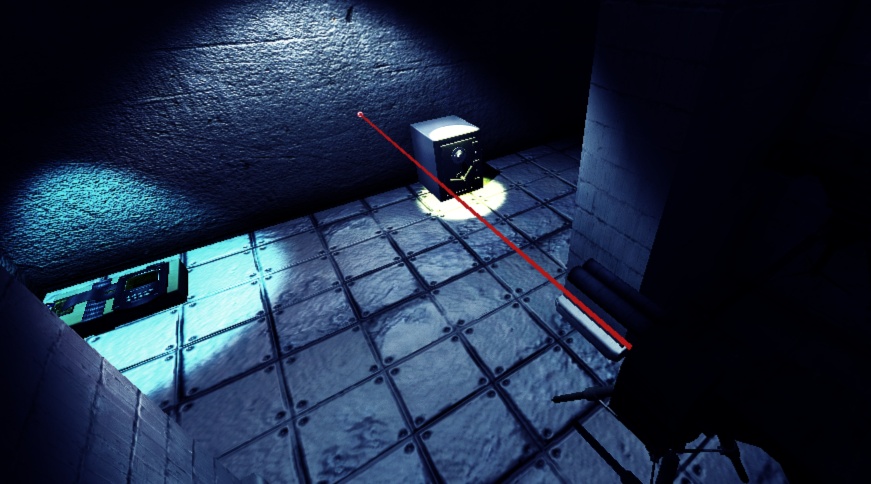

Since it is not powered by electricity , it can remain enabled for indefinite periods of time.
Due to certain budget issues however it is only available through unlocking it via spending points that you can acquire by completing objectives or opening crates.
The WEC Black Market will also accept refunds for this specific product.
#3 - Safes: Another old school means of security, the safes are containing devices with a non-electronic lock, meaning they cannot be hacked or intruded via a network, leaving no alternative to breaking into them the old fashioned way.

The lock is controlled by a numbered rotation mechanism; the user must rotate the handle clockwise so as the first number of the four-number code faces upwards. The user must then repeat the proccess while rotating the handle in the opposite direction each time they reach the needed number.
All of our agents are equipped with a unique listening device that boosts their hearing capabilities, this device is crucial to the safe's cracking. Upon reaching a correct number, the lock mechanism produces a different sound as it readies a part of the lock to be opened, the listening device allows the user to easily detect the change of sound and easily break into the safe.
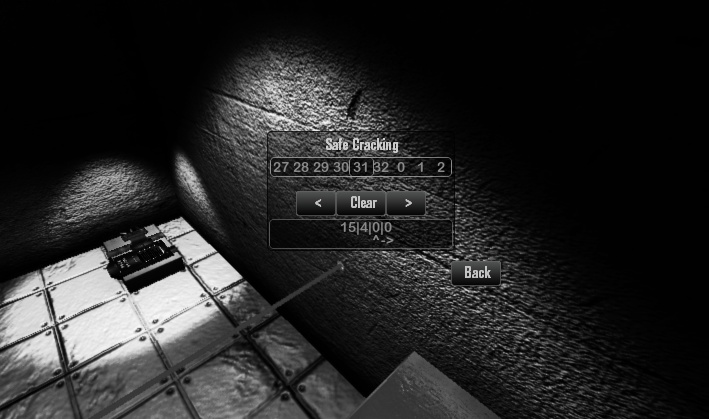
Safes usually contain keys that are used to open crates for points; a highly valuable asset that should be acquired whenever possible.
To Be Continued in Part 2.


