Hacking has been around since early pre-alpha 2013, and while the early Alpha releases have dozens of commands you can use to achieve various effects, I've always considered the system a work in progress. There are more things that can be hacked, a few tweaks and changes to expect, and furthermore there are three major categories of hacks, and before Alpha 4 we'd only seen the first!
- Common hacks. Most of these are commands native to the system itself, functions and data that Operators and other robots need access to for their work. There are currently 54 of these.
- Unauthorized hacks. The topic of this post. Alpha 4 contains 11 of these.
- Unique hacks. NPCs will under special circumstances, or for plot purposes, give codes that can be used to achieve unique effects. These would of course always be entered manually. (There are actually a number of these coded in the game--originally added to test the implementation and ensure it works--but no way for players to discover them yet =p)
These three categories run the spectrum from common to obscure, in that order. So with Alpha 4 we've begun exploring the second category. Don't worry, there are still more improvements and features to come in category 1.
The concept of "unauthorized hacks" was first introduced in relation to Garrison Access systems. These are hacks that attack the system itself or abuse it in some way, decidedly not what you're supposed to be doing there. They are always entered manually--you'll never see these listed like the others.
SPOILER WARNING: Beyond this point I'll be revealing how to do each hack and how they work, even though you're meant to learn all this via in-game lore! However, right now the necessary lore only exists for one of these hacks--respective lore for the others cannot be added until I create the part of the world where much of it will be found. Reading this will allow you to get around that temporary roadblock and check out this new content, but doing so doesn't make it any less spoilery! Your choice :)
Unauthorized hacks can be divided into two sub-categories...
Trojans
With Trojans you install a program that runs on the target system to provide delayed or continuous long-term benefits. You'll want to make sure the machine itself isn't disabled, since that will of course render the Trojan useless. Once planted Trojans will continue to operate even if you are traced, however.
There are eight Trojans so far, affecting either Terminals or Garrison Access systems.
Terminal Trojans:
- Trojan(Track): Reports to you the current location of all robots within a square zone around the terminal, as if you were standing there with sensors and an Adv. Signal Interpreter. The area of effect is determined by the security level of the Terminal--higher tier systems have a greater range.
- Trojan(Assimilate): An Operator attempting to use this Terminal will instead be permanently converted to an ally (to join your personal hacker network :D).
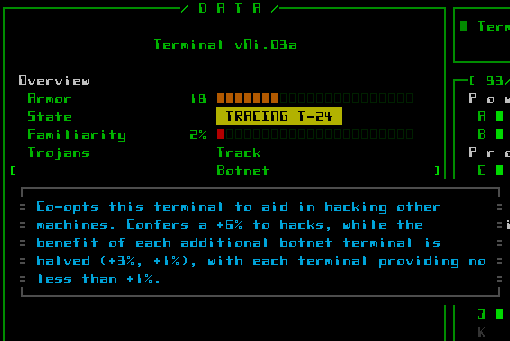
- Trojan(Botnet): As long as this terminal is active, it provides a bonus to both direct and indirect hacks at any other machine on the same floor. This effect stacks across multiple infected Terminals (with diminishing returns, in the same way multiple allied Operators stack). Build your own network!
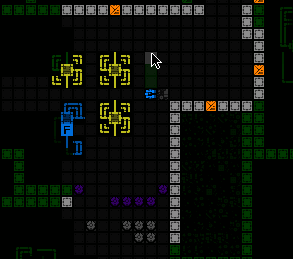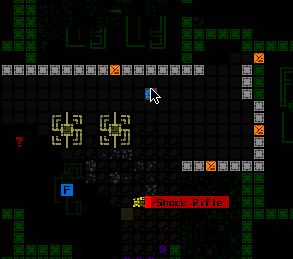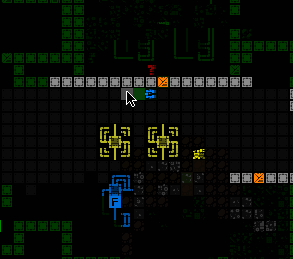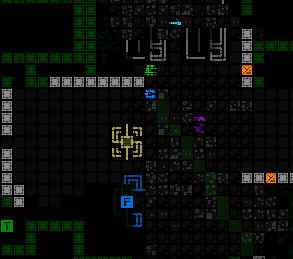
Installing a Botnet Trojan at a terminal.
Machine info lists the currently active Trojans, and allows you to call up context help for each.
- Trojan(Detonate): Sets all explosive machines within the Terminal's zone of influence to explode immediately when your enemies pass by. Create your own oversized minefield!
Oops, Mr. Programmer, looks like you should've taken a left at the Subcomponent Replicator. (Nuclear Reactors previously infected by the Detonate Trojan--they glow yellow so you know/remember which ones they are).
Garrison Access Trojans:
- Trojan(Broadcast): Any squad dispatched from this garrison will have its type and composition reported to you immediately, and their location added to your intel database for reference.
- Trojan(Decoy): The next squad dispatched from this garrison will have its intended target switched to somewhere/something else at the last moment.
- Trojan(Redirect): All squads dispatched from this garrison have their target altered (more difficult than a one-off decoy).
- Trojan(Reprogram): The entire next squad to emerge will be converted to loyal followers!
Brute Force
A "brute force" hack completely disregards stealth and overwhelms the target system to achieve some effect, rendering it useless in the process (permanently locked). While brute forcing a system is guaranteed to attract attention, it's quite easy to do and allows for some more extreme benefits.
Three different machines are currently susceptible to brute force attacks.
- Force(Extract): At any Scanalyzer, extract from the system's memory a number of schematics for parts previously scanned by other robots. You can't control the results, but if lucky it can be fairly useful.
- Force(Jam): Use this to prevent a Garrison Access system from opening the door for any squads trying to exit into the local area. This is the easiest way to cut off access from a garrison, but is also the most meddling from the enemy's point of view, a third-rate option behind the much more difficult Seal hack, or simply blasting the Garrison Access system.
- Force(Overload): For those of you who don't have much need of Fabricators, how about turning them into engines of destruction? :D This very unauthorized hack causes the machine's EM imprinting system to go haywire, randomly zapping passing robots with corrupting beams of energy. Use only with intent to cause maximum chaos. And you'd better get out of the way! (This is the one which has already been added to the lore, so I didn't really have to mention it here, but may as well for completeness sake--plus it's the most fun =p)
There's plenty of room for more unauthorized hacks in the future. This first batch was just a medium-sized "side project" alongside Garrison Access, to enable some additional strategic options for that machine.


So, given an infinite amount of time, by entering a bunch of random strings, one could conceivably find a hidden code implemented but not mentioned? seems like i have my weekend ahead of me ;)
Hahaha...does your weekend somehow contain an infinite amount of time? :)
Seriously, in theory, yes, though doing so would be quite annoying since you're traced quickly. All will be discoverable when the time comes. In a recent stream of the game I showed one of the secret hacks, but it's a pure Easter Egg with no meaningful use. There are a few others with interesting effects--two of them give you viruses "which are pretty cool" :D. I haven't started working on that third category for real because it's dependent on story/NPCs which have only just begun to be added.
All unauthorized hacks, on the other hand, have been revealed via/as of this post. I've already come up with some new ones I'd like to add soon, but may not announce them.